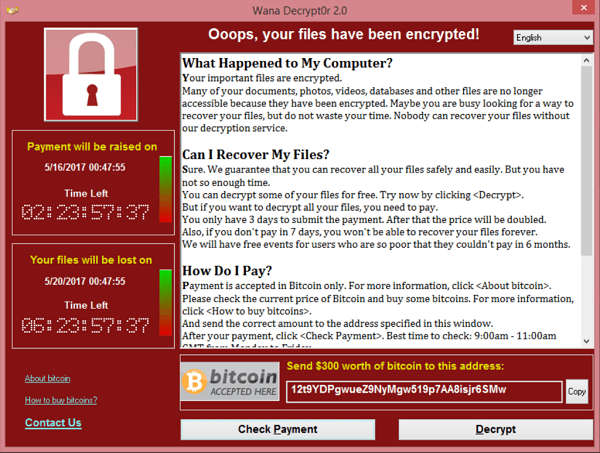
When you open your newspaper, chances are pretty high that there is yet again an item or even a headline on cyber-attacks. Especially ransomware cyber-attacks are omni-present these days. These attacks lock people’s computers and their data where after users are asked to pay a ransom in order to get their files and systems back.
Recent examples are Asco, a Belgian company in the aerospace industry with 1.500 employees in Belgium, Germany, Canada and the US, that got hit by a Ransomware attack in June 2019 and lost its entire production capability for almost a month and is still recovering today. More recently, the University of Maastricht got hit and lost the bulk of their Windows-based systems, causing an interruption in their teaching activity, and in the end had to pay the ransom in order to get their systems back.
The story of these articles is usually the same, impacted companies lose their ability to do business and to run their operations, hereby impacting their profit, their employees and the reputation of the organization in the long-term.
This news coverage is good for creating awareness about this growing problem, but they rarely help you to understand how to avoid this problem in the first place, and how to properly respond to such an attack if you become a victim yourself.
Before we dive into avoiding and responding to ransomware attacks, it is important to understand what ransomware is, how it operates, who is behind it and what is their motivation.
The majority of ransomware attacks are driven by financial gain, only a minority have sabotage in mind.
Financially driven attacks are usually executed in an opportunistic fashion by organised crime or malicious individuals that want to make as much money as possible with the least effort by making as many potential victims with a single attack, going for the lowest hanging fruit first. If the attack is sabotage driven, it is typically targeted and more sophisticated to damage the specific organization and its operations.
Each ransomware attack starts with a piece of malicious software (malware) that the attacker wants to deploy on your system to take over control. The attacker has various ways of doing this, which are called attack vectors:
- Exploits: These are malicious software tools that abuse known unpatched and unknown vulnerabilities on your system. These exploit tools – also called exploit kits – are usually executed when a potential victim visits a website that got compromised. Malicious software hidden on the site or in an advertisement will redirect you unnoticed and when your system is vulnerable, a drive-by download of the ransomware malware is executed, and your system becomes infected.
- Phishing with malicious email attachments and links: An attacker crafts emails, likely from a trusted source and with familiar content, and attaches a malicious file that looks like a normal document. When you open the attachment, the ransomware malware is installed or downloaded, and your system becomes infected. Like attachments, the attacker can also embed links (URLS) in the email and lure you into visiting these links. When clicked, the link will download the malware and your system becomes infected too.
- Downloads: Ransomware can also be hidden in downloads executed by yourself when they come from an untrusted or compromised source. When opened, the malware will be installed and infect your system.
- USB drives: Like downloads, the malware can also hide on compromised USB drives and when plugged in, the malware will try install and infect your system.
- Network: Some types of malware can spread through the network by exploiting known unpatched and unknown vulnerabilities in the network protocols used by your system. This means that if an already infected machine is connected to your network, the ransomware can infect any unpatched system that is connected to the same network if no other protections are in place. Usually, they have the ability to propagate lighting fast. An example of this is the WannaCry ransomware which infected and brought down hundreds of thousands of machines in a matter of days and caused a major disruption in UK hospitals.
Once the malware is on your system, it will phone home to a Command and Control (C&C) server on the internet, where it will get instructions from the attacker on what to do next. At this stage and given the attacker has control over your system, a few things can happen in parallel or sequential:
- The malware encrypts your files with an encryption key only known to attacker, this could include connected USB and network drives and even connected backup systems;
- The malware looks for sensitive information that could be used for extorsion, or for re-selling on the black market when it concerns valuable intellectual property, credit card information, or customer data. Some attacks will also look for crypto-currency wallets that might exist on the infected system and can be transferred to the attacker;
- The malware starts looking for other systems on your network or systems directly attached to your system and will try to infect them too, where after the same actions can be applied as with the initial host system. This is called lateral movement. With lateral movement, it’s usually the attacker’s goal to obtain as much access to as many systems within the organisation. Especially the organisation’s domain controllers are seen as the keys to the Kingdom. Systems controlling production installations are also highly targeted as they can wreak havoc to a company’s business, making the victim more willing to pay the ransom;
- In some cases, the attacker can also use your infected infrastructure as a starting point to hack into your customers or suppliers that are connected through e.g. shared private networks, applications, documents or by sending out phishing emails originating from your organization.
How can I prevent all of this?
Preventing ransomware attacks requires a layered approach that involves technology-based controls, user awareness and training, in combination with the right IT policies, procedures and processes that together form the basis of a good cyber security hygiene. This will help you not only preventing ransomware attacks but increase your overall cyber resilience, and it will help you recover from an attack more rapidly while limiting the impact to your business.
- Train your staff regularly on how to use IT systems responsibly based on company policies and how to recognize phishing attempts. Educate them to never click on unverified links, open untrusted email attachments, download files from unknown sites, connect unfamiliar USB-drives, or hand-over personal data, including usernames and passwords;
- Protect each end-point system with up-to-date end-point protection software (e.g. anti-virus, anti-phishing, web-protection);
- Patch/update all software in your environment regularly, including operating systems, network devices, applications, mobile phones and other software frequently. A lot of ransomware attacks are still successfully exploiting system vulnerabilities that are known and for which a patch is available for many months;
- Backup – Probably the most important countermeasure against Ransomware is backing up all systems, also including your securely configured cloud storage. These regular backups should be stored at a different location and should be isolated from the overall network, so that any infection could be prevented from spreading to the backup. These backups and their recovery should be regularly tested, including the integrity of backups;
- Control your email, web and remote access – The organisation’s email and web access should be configured to scan and limit the type of attachment and downloads that are coming in (e.g. office files with Macro’s enabled or JavaScript), stop executable file downloads, and detect and prevent access to known bad sites, URLs and scripts. Ideally, all incoming external mail is also tagged as EXTERNAL to inform the user that she/he has to be more vigilant;
- Access to systems and network drives should be based on a least access privilege mechanism, so that a regular user and his/her system don’t have full control over it as it would give also full access to any malware infection. Where possible, strong authentication mechanisms should be implemented;
- Monitor your environment, this might not immediately detect and stop the initial infection, but it will be help you to detect any lateral movement and malicious behaviour in your organisation early and will allow you to react more quickly, limiting any further damage;
- Have an incident response plan ready for ransomware. Knowing what to do and who to contact in case of an attack is key in trying to limit the impact of the attack.
What to do if you are under attack
You have carefully followed the guidelines above but still all of sudden your screen looks like this?
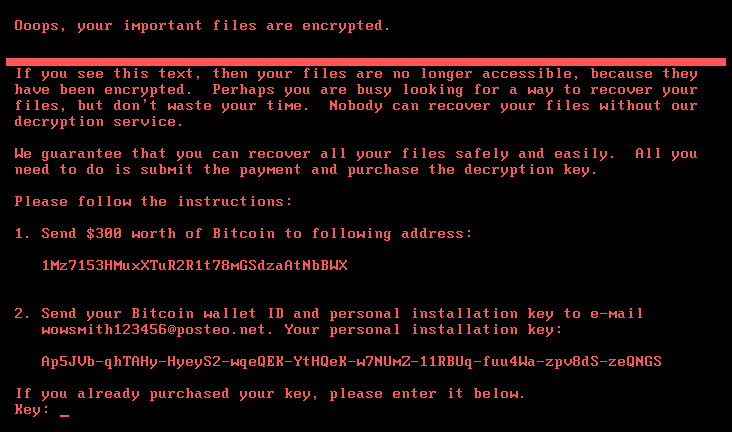
What should you do? First of all, don’t panic. Even if the situation looks terrible at first glance, it is key to remain calm in order to do the right thing to get you out of despair.
- First of all, disconnect the impacted system from the network and turn off any wireless functionality;
- Determine the scope of infection – only one system, or also network drives/folders, external hard drives, storage devices, servers, etc. It might be necessary to investigate if there wasn’t a data breach as well. If this is the case, it might be mandatory to inform law enforcement and external parties involved in the breach;
- Determine the type of ransomware and to check for decryption possibilities. For some known ransomware, the encryption key is publicly available or can be bypassed in the meanwhile via what is called a decryptor tool. With this tool, you can get your files back without paying the ransom. A list of tools can be found at https://www.nomoreransom.org/;
- When a backup is available and when you are sure all infected systems are taken off the network, you can restore the systems and files from backup. If you restore a backup, do it while the system is isolated from the rest of the network and patch the system first after backup restoration. This to prevent re-infection after a successful restore. Also make sure that the backup you are restoring is clean from malware so that you don’t accidently re-infect yourself;
- In the unfortunate event that a backup is not available, your business is in danger and you are sure it is not a sabotage driven ransomware, it might be necessary to negotiate or pay the ransom. Although we don’t recommend this by default, as there is no guarantee that you will get your files back and you will also keep their business model in the air, sometimes there is just no other option than paying the ransom in order to save the business;
- In the event you paid the ransom and you received a decryption key to unlock your locked systems or files, it is still necessary to re-build your environment to make sure that attacker is out of your network, also changing all systems and user credentials. Once systems have been re-build, you should do an integrity check of your data, and the environment should be closely monitored for new malicious behaviour;
- Last but not least, learn from the incident and investigate how you could prevent similar attacks in the future and to make yourself more cyber resilient.
Cybercrime and more in particular ransomware are here to stay and will even grow in a world where each and everything gets interconnected, especially with the introduction of 5G networks allowing much more physical applications. Hence you should not ask yourself whether or not you will become a target of a cyber-attack, instead it is a question of when you will be hit and how well prepared you are to prevent, to early detect and to rapidly respond to such an incident, avoiding damage to your organisation, employees and your customers.
Still uncertain about your cyber resilience against ransomware? Don’t hesitate to contact us!
Say what? IT jargon explained.
- Drive-by download: A drive-by-download refers to the unintentional download of a piece of malicious software to your mobile device or computer. You don’t have to click or press download anywhere, just the act of visiting a site is enough to get the software on your device.
- Phishing: Phishing is the practice where an attacker masquerades himself as a reputable entity or person in email, instant messaging, telephone conversations or other communication methods and then tries to trick a user in divulging sensitive information such as usernames, passwords, personal details or getting a user to actively do something such as clicking a link.
- Patching: A patch is a piece of software that is used to fix issues with your mobile device, computer or the software installed on it. In the case that software vulnerabilities are discovered in the applications you use, the application vendor issues a patch that the user or system administrator can install to fix the vulnerability. Installing or updating your software with these patches is called patching. A system that is running software that has known vulnerabilities and where a patch hasn’t been installed on yet is often described as an ‘unpatched’ system. A good example of patching are the regular windows updates which fix security vulnerabilities in Microsoft Windows.
- End-point system: An end-point is a computing device that communicates back and forth with a network to which is it connected. Examples of endpoints include Desktops, Laptops, Smartphones, Tablets, Servers, Workstations. Endpoints represent key vulnerable points of entry for cybercriminals as this is where a user is actively interacting with the device.
- Least access privilege: The principle of least access means that a user should only be given as much access to information assets (computers, files, apps,…) needed to perform his job. While it might be easier to grant a user in an organization ‘any’ access, that would mean that he has more access than he actually needs and in the case his machine or his access gets compromised, that access will be abused by an attacker. Therefore, limiting users and systems to the data, applications and systems they need is considered a best practice in IT security to make it harder for attackers to gain full access to an IT environment.
- Strong Authentication: Strong Authentication is any method of verifying the identity of a user or device in such fashion that the authentication verification mechanism can withstand attacks. Typically, this is accomplished by Multi-Factor Authentication. Multi-Factor authentication is an authentication method where a user or system is only granted access after presenting at least two pieces of evidence (factors) for his identity. This is in most implementations something you have (i.e. a number generator on your phone, a key card or a fingerprint) and something you know (i.e. a password or a PIN code)
- Integrity check: An integrity check is where you compare the stored data (i.e. backup data) to the state of the data you expect it should be. This is a good practice to detect if there are any unexpected changes (i.e. due to corrupted backups) so you are sure you have a working set of information that you can trust.