For many organizations, it’s no longer viable nor desired to deliver and manage all aspects of IT entirely in house, especially services that require advanced skills and are expensive to operate are hard to keep inhouse. Operating a 24/7 Security Operations Center (SOC) for cyber incident detection and response is such a service but how do you successfully partner up with a Managed Security Services Provider (MSSP)?
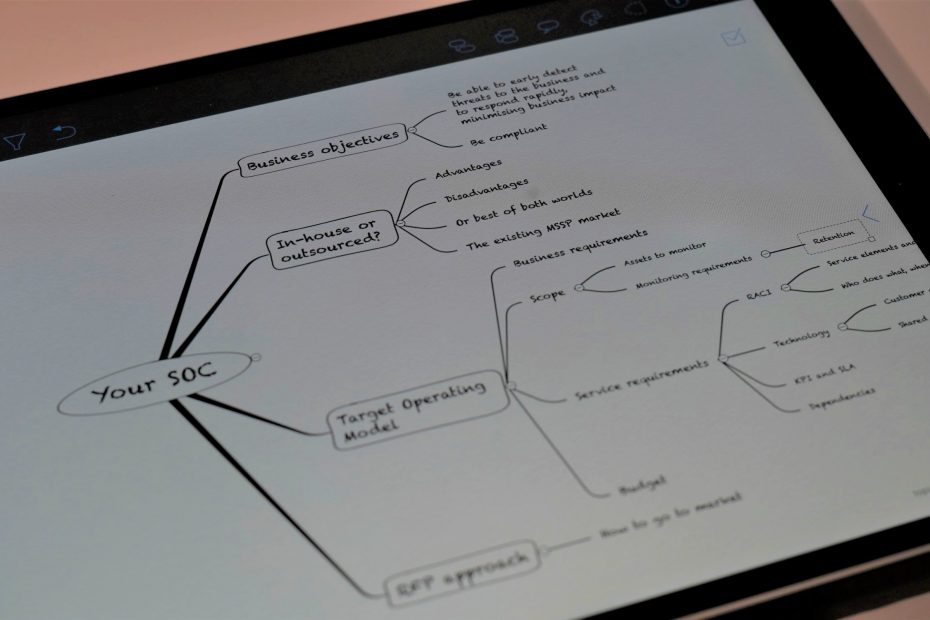
Your Target Operating Model
This is where a Target Operating Model (T.O.M.) comes into play. A Target Operating Model describes the desired business outcomes of the service, the service elements from a people, process and technology perspective, the journey to get there, while considering internal and external compliance requirements, existing internal capabilities, and budget.
Trying to protect and monitor every asset at the same level is nearly impossible and is not cost-effective. Hence the initial focus of your SOC should be on your company’s critical business processes, the threats that could pose a risk to them, and listing the IT assets these processes are depending on. Based on the identified IT risks to the business, you can create a prioritized list of IT assets that need to be monitored, both from a security and compliance perspective. This will form the baseline of your T.O.M..
A SOC is built on People, Processes, and Technology and so should be your Target Operating Model
Although each organization is unique, that doesn’t usually mean that it also requires entirely unique SOC services. Hence an important step in defining your T.O.M, is to explore what the MSSP market has to offer and at what cost. A good and a financially healthy MSSP will build its services in a scalable way, meaning that 80% of its services and deliverables are standard and shared amongst all of its customers while only 20% or less of the deliverables are tailored to specific customer demands. This way, the MSSP can guarantee a consistent quality at an acceptable price-point. So, unless your organization really has unique security requirements, it is advised to align your Target Operating Model to existing MSSP offerings and their cost drivers, making sure that you will stay within your budget.
The RACI Approach
People and how they operate are the key assets of your SOC. By mapping out all service elements and underlying tasks you require to adequately protect your business, in combination with your internal capabilities and desired capabilities in a RACI matrix you will have a solid blueprint of the service elements, people and skills you need and how your SOC needs to look like. Such a RACI matrix describes which team is Responsible, Accountable, Consulted and Informed for each task and provides a clear overview to potential MSSP partners of what service elements and tasks are to be delivered and with whom they should work for a given task. This approach also creates a level playing field between the various providers, allowing you to see which elements are part of the provider’s standard services, or whether they are optional or limited in time or effort.
Monitoring scope
Next to the service elements and tasks required in the RACI, the effort to be delivered by the MSSP is also determined by your monitoring scope – derived from your prioritized list of IT assets that need to be monitored – and associated monitoring needs such as expected incidents to be investigated, data volume and retention. Hence in order to further complete your T.O.M, you will need to create a list of all systems that need to be monitored in combination with their monitoring needs. Since a SOC builds its knowledge and maturity about an organization’s environment over time, we always recommend cutting the monitoring scope in smaller blocks or waves of assets. This will save on cost and avoids that the SOC gets buried under a pile of events.
Technology
A SOC can’t operate without an underlying technology layer to collect and store data, to detect threats to your environment and to respond to incidents in a fast and adequate manner. Do you buy your own technology stack, and have it managed by the MSSP or do you let the MSSP choose which technology to use?
Operating security monitoring technology is not a trivial task as it is being fed by a plethora of systems of all kinds and requires considerable effort. Therefore, most MSSPs standardize their offering around one or two technology solutions that can be scaled via e.g. multitenancy or build their own solution. When you mandate a certain technology stack, be aware that you will limit the number of providers that can offer the service. On top, MSSPs that operate separate technology instances per customer typically have a higher internal cost and higher price than providers that work with multi-tenancy platforms that are easier to maintain and more cost-effective.
The advantage of having your own stack is that it will be easier to switch provider at the end of the contract but the question that pops to mind in that case is whether or not the technology will still be up to date at that moment in a fast changing market.
Our recommendation is not to mandate the technology but to list the required functionalities and to ask for full read-only access to the platform and the ability to keep all contextual intellectual property at the end of the contract such as playbooks, use-cases, reports, etc. that have been created for you.
KPI and SLA
Each good MSSP provides Key Performance Indicators (KPIs) and Service Level Agreements (SLAs) but it is key to assess their applicability to the service. Service availability and escalation SLAs are common practice but these are easily achieved in a security monitoring context. Measuring the ongoing quality of use cases, SOC investigations, and other key tasks is a lot harder and you should question your future MSSP on this.
Bringing it all together
When you bring the business requirements, the monitoring scope and needs, the detailed RACI, your technology needs, and your KPI and SLA requirements together, you will have defined your Target Operating Model. You can share this with potential MSSPs to get a proposal from them and it can be used for internal stakeholder management and alignment.
Do you want to know more about how to successfully design your own Target Operating Model and how to select your own MSSP partner, don’t hesitate to get in contact with us!